Software Dowsstrike2045 Python – Advanced Cybersecurity & Automation

The digital world is evolving rapidly, and cybersecurity threats are becoming more complex. AI-driven attacks, ransomware, and automated hacking are becoming increasingly sophisticated, thereby increasing the risk to organizations. To stay protected, companies need powerful, flexible tools that defend against threats while streamlining security operations.
Software Dowsstrike2045 Python is a next-gen, Python-based framework that combines cybersecurity, automation, and AI intelligence into a single platform. It provides a versatile solution for protecting networks, monitoring threats, and simulating attacks.
This article explores its key features, applications, and impact, showing why it’s becoming essential for modern cybersecurity professionals.
What Is Software Dowsstrike2045 Python?
It is a Python-powered framework aimed at ethical hackers, cybersecurity professionals, and researchers. It blends automation, real-time monitoring, penetration testing, and AI-assisted threat detection into a modular platform.
The concept embodies the vision for intelligent cybersecurity systems, preparing organizations for future threats up to 2045.
Key objectives include:
Why Python Is The Backbone?
Python powers it for several reasons:
- Simplicity: Its readable syntax accelerates development and learning, reducing errors in critical security scripts.
- Versatility: It supports integration with libraries for AI (PyTorch, TensorFlow), network analysis (Scapy, Nmap), and visualization (Matplotlib, Plotly).
- Scalability: It is suitable for small-scale testing and large enterprise deployments.
- Automation Ready: It has built-in modules that allow orchestration, scripting, and real-time monitoring, enabling proactive defense measures.
Python’s broad ecosystem makes the framework both accessible to beginners and powerful for professionals. Channeling Oxzep7, Dowsstrike2045 turns Python frameworks into scalable, next-gen solution hubs.
Core Features Of Software Dowsstrike2045 Python
Network Scanning & Vulnerability Detection
The framework integrates with Nmap, Scapy, and Metasploit to detect vulnerabilities, map network topologies, and identify potential entry points. It allows both automated and manual scanning for thorough network security assessments.
Automated Threat Response
AI-driven triggers monitor system activity, detect anomalies, and execute automated defense strategies. This reduces the response time from hours to seconds, critical for preventing breaches in high-stakes environments.
DDoS Mitigation Engine
DDoS attacks can cripple networks. The framework continuously monitors traffic, recognizes unusual patterns, and deploys mitigation scripts such as SYN flood detection and UDP filtering to ensure uninterrupted service.
Simulation & Training Modules
AI personas simulate attackers, defenders, and neutral agents for hands-on learning. These virtual scenarios help cybersecurity teams practice real-world defense strategies, test new tools, and prepare for ethical hacking exercises.
Data Visualization & Analytics
Real-time dashboards, charts, and reports provide actionable insights on network activity, detected vulnerabilities, and AI decision-making processes. Users can export reports in JSON, CSV, or XML for documentation or compliance.
Modular Architecture
The plugin-driven design allows developers to add custom modules, integrate with external tools, and tailor the system for specific industry needs without affecting the core framework.
Installation & Setup
Prerequisites
- Python 3.9 or higher: It ensures you have the latest stable Python version to take full advantage of all framework features and libraries.
- Pip package manager: It is required for installing Dowsstrike2045 Python and any additional dependencies seamlessly.
- Virtual environment recommended: Using a virtual environment keeps project dependencies isolated and prevents conflicts with other Python packages on your system.
- Stable Internet connection: It needed to download packages, updates, and integrate external tools smoothly.
Installation Example
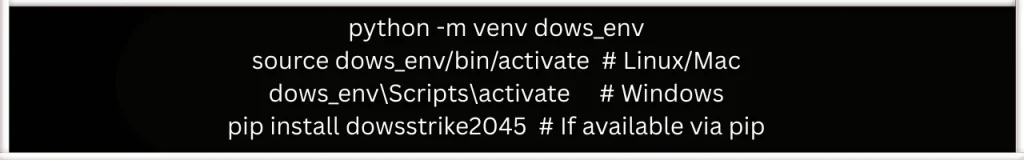
First Test Script
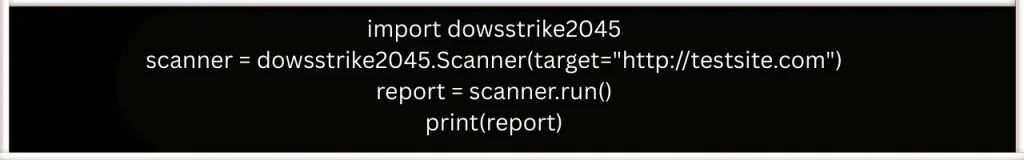
Community, Collaboration, & Ethics
The framework also promotes collaboration among cybersecurity pros, researchers, and learners. Its modular tools encourage experimentation while highlighting ethical AI use. By combining skill-building and responsible practices, it helps create a stronger, more aware cybersecurity community.
Integration Possibilities & Compatibility
| Integration Type | Compatible Tools / Platforms | Key Benefit |
| Cybersecurity Tools | Nmap, Scapy, Metasploit | Seamless vulnerability scanning & testing |
| AI & ML Libraries | PyTorch, TensorFlow | Enhances predictive threat detection |
| Cloud Platforms | AWS, GCP, Azure | Secure cloud deployments & monitoring |
| DevOps Pipelines | Jenkins, GitLab CI/CD | Automates security in development workflows |
| Visualization Tools | Matplotlib, Plotly | Real-time dashboards & analytics |
| Quantum Computing Prep | Qiskit, Cirq | Supports future-proof encryption & simulations |
Advanced Modules & Integration
AI And Machine Learning Integration
AI algorithms predict emerging threats by learning from network behavior patterns. Reinforcement learning models enable adaptive decision-making and proactive defense.
Quantum Computing Preparedness
As quantum computing grows, it envisions libraries to handle high-speed computations, enabling advanced encryption and predictive security models.
Automation & Workflow Optimization
Automated scripts reduce repetitive tasks such as scheduled scans, real-time alert handling, and report generation, freeing cybersecurity teams to focus on strategic decisions.
The way modern tools cut friction in workflows, Dowsstrike2045 applies automation to optimize security.
Explore Zardgadjets Guide – Where Digital Productivity Meets Automation Power
Cloud & Devops Integration
The framework can integrate with cloud services (AWS, GCP) and CI/CD pipelines, enabling security automation in modern DevOps environments.
Use Cases
- Enterprise Security: Continuous monitoring, automated threat detection, and vulnerability management.
- Red Team Exercises: Simulated attacks and penetration testing for training cybersecurity personnel.
- Educational Platforms: Hands-on learning for students and professionals, fostering a skilled workforce.
- AI Experimentation: Testing AI behavior and ethical compliance in controlled virtual environments.
- Financial Sector: Fraud detection, secure transactions, and automated compliance monitoring.
You can get the complete details about how Refixs2.5.8a brings the ultimate update for performance and security.
Advantages Of Software Dowsstrike2045 Python
- Modular and scalable architecture: Designed with flexible modules that can be easily adapted or expanded to meet varying cybersecurity needs.
- AI-powered adaptive threat detection: Uses intelligent algorithms to identify and respond to emerging threats in real time.
- Real-time monitoring and automated response: Continuously tracks network activity and automates defensive actions for faster threat mitigation.
- Integration with popular cybersecurity tools: Compatible with tools like Nmap, Scapy, and Metasploit, enabling comprehensive security workflows.
- Supports training, research, and enterprise deployment: It is useful for academic programs, professional training, and large-scale organizational security operations.
You can also learn to Download Clienage9 for PC to enjoy smarter productivity and smoother performance.
Limitations
- No fully verified official release yet: The framework is largely conceptual, with no confirmed GitHub or PyPI repository available.
- Primarily CLI-based with limited GUI support: Most operations require command-line usage, which may be challenging for users preferring graphical interfaces.
- Requires intermediate to advanced Python skills: Effective use of the platform demands strong programming knowledge and scripting experience.
- Risky if downloaded from untrusted sources: Attempting to install unofficial versions could expose systems to malware or security vulnerabilities.
The Zeeroq breach showed the stakes frameworks like Dowsstrike2045 are essential shields against massive cyber threats.
| Pros | Cons |
| AI-powered Automation | Unverified Release |
| Modular and Scalable | Needs Strong Python skills |
Conclusion
It represents a groundbreaking approach to integrated cybersecurity, automation, and AI-driven threat management. Its modular architecture, real-time monitoring, intelligent AI personas, and adaptability make it a highly versatile platform suitable for both educational purposes and professional cybersecurity operations.
Even though an official release is still pending, the framework’s concept is already influencing the industry by promoting unified, intelligent, and proactive security strategies.
By exploring and understanding it, organizations and students can better prepare for increasingly complex cyber threats and evolving digital challenges.





